# Initial Harbor tasks
YouTube video: https://youtu.be/DcArQEFgk5s (opens new window)
Let's do some initial Harbor configuration on second Harbor instance: https://harbor.mylabs.dev (opens new window)
If you are using Let's Encrypt "staging" you need to download and use their "Fake LE Root X1" certificate for curl, helm and k8s cluster:
test -d tmp || mkdir tmp
cd tmp
if [ ${LETSENCRYPT_ENVIRONMENT} = "staging" ]; then
sudo mkdir -pv /etc/docker/certs.d/harbor.${MY_DOMAIN}/
CA_CERT=$(kubectl get secrets ingress-cert-staging -n cert-manager -o jsonpath="{.data.ca\.crt}")
[ "${CA_CERT}" != "<nil>" ] && echo ${CA_CERT} | base64 -d > ca.crt
test -s ca.crt || wget -q https://letsencrypt.org/certs/fakelerootx1.pem -O ca.crt
sudo cp ca.crt /etc/docker/certs.d/harbor.${MY_DOMAIN}/ca.crt
export SSL_CERT_FILE=$PWD/ca.crt
for EXTERNAL_IP in $(kubectl get nodes --output=jsonpath="{.items[*].status.addresses[?(@.type==\"ExternalIP\")].address}"); do
ssh -q -o StrictHostKeyChecking=no -l ec2-user ${EXTERNAL_IP} \
"sudo mkdir -p /etc/docker/certs.d/harbor.${MY_DOMAIN}/ && sudo wget -q https://letsencrypt.org/certs/fakelerootx1.pem -O /etc/docker/certs.d/harbor.${MY_DOMAIN}/ca.crt"
done
echo "*** Done"
fi
Output:
# LDAP Authentication
List users which are in Active Directory:
ldapsearch -LLL -x -h winad01.${MY_DOMAIN} -D cn=ansible,cn=Users,dc=mylabs,dc=dev -w ansible_secret_password -b cn=users,dc=mylabs,dc=dev -s sub "(cn=aduser*)" dn name description memberOf
Output:
dn: CN=aduser01,CN=Users,DC=mylabs,DC=dev
description: User 01 - Group 01
memberOf: CN=adgroup01,CN=Users,DC=mylabs,DC=dev
name: aduser01
dn: CN=aduser02,CN=Users,DC=mylabs,DC=dev
description: User 02 - Group 01
memberOf: CN=adgroup01,CN=Users,DC=mylabs,DC=dev
name: aduser02
dn: CN=aduser03,CN=Users,DC=mylabs,DC=dev
description: User 03 - Group 02
memberOf: CN=adgroup02,CN=Users,DC=mylabs,DC=dev
name: aduser03
dn: CN=aduser04,CN=Users,DC=mylabs,DC=dev
description: User 04 - Group 02
memberOf: CN=adgroup02,CN=Users,DC=mylabs,DC=dev
name: aduser04
dn: CN=aduser05,CN=Users,DC=mylabs,DC=dev
description: User 05 - Group 03
memberOf: CN=adgroup03,CN=Users,DC=mylabs,DC=dev
name: aduser05
dn: CN=aduser06,CN=Users,DC=mylabs,DC=dev
description: User 06 - Group 03
memberOf: CN=adgroup03,CN=Users,DC=mylabs,DC=dev
name: aduser06
List groups which are in Active Directory:
ldapsearch -LLL -x -h winad01.${MY_DOMAIN} -D cn=ansible,cn=Users,dc=mylabs,dc=dev -w ansible_secret_password -b cn=users,dc=mylabs,dc=dev -s sub "(cn=adgroup*)" dn name description member
Output:
dn: CN=adgroup01,CN=Users,DC=mylabs,DC=dev
description: AD User Group 01
member: CN=aduser02,CN=Users,DC=mylabs,DC=dev
member: CN=aduser01,CN=Users,DC=mylabs,DC=dev
name: adgroup01
dn: CN=adgroup02,CN=Users,DC=mylabs,DC=dev
description: AD User Group 02
member: CN=aduser04,CN=Users,DC=mylabs,DC=dev
member: CN=aduser03,CN=Users,DC=mylabs,DC=dev
name: adgroup02
dn: CN=adgroup03,CN=Users,DC=mylabs,DC=dev
description: AD User Group 03
member: CN=aduser06,CN=Users,DC=mylabs,DC=dev
member: CN=aduser05,CN=Users,DC=mylabs,DC=dev
name: adgroup03
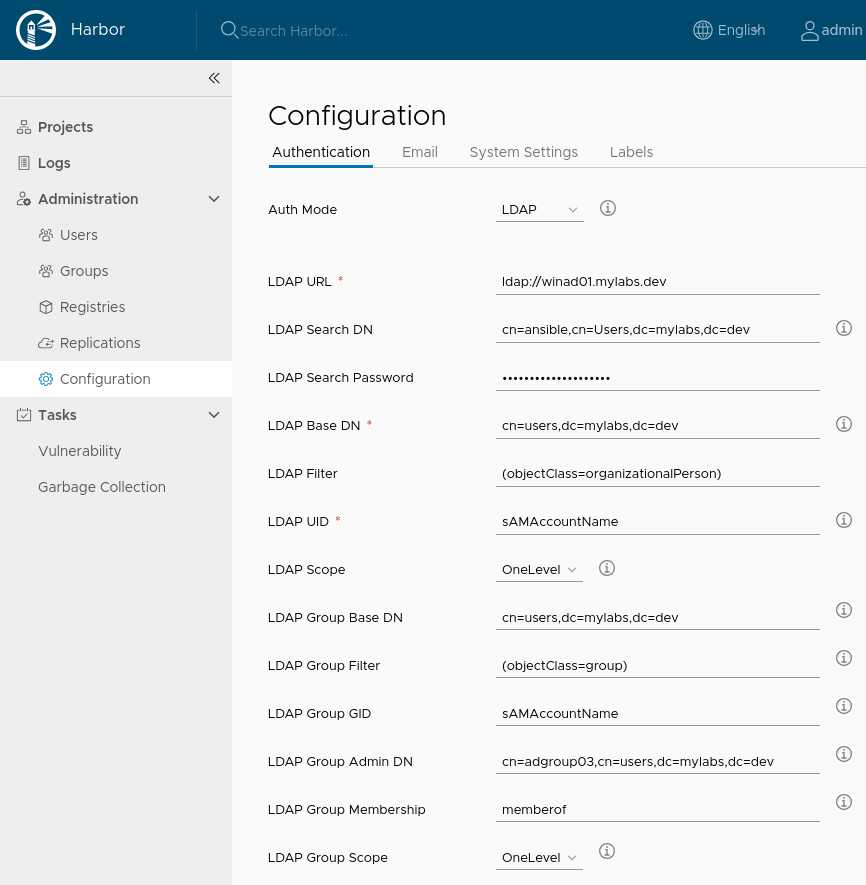
Configure LDAP/Active Directory authentication in Harbor by going to
Administration -> Configuration -> Authentication:
Auth Mode: LDAPLDAP URL: ldap://winad01.mylabs.devLDAP Search DN: cn=ansible,cn=Users,dc=mylabs,dc=devLDAP Search Password: ansible_secret_passwordLDAP Base DN: cn=users,dc=mylabs,dc=devLDAP UID: sAMAccountNameLDAP Scope: OneLevelLDAP Group Base DN: cn=users,dc=mylabs,dc=devLDAP Group GID: sAMAccountNameLDAP Group Admin DN: cn=adgroup03,cn=users,dc=mylabs,dc=devLDAP Group Scope: OneLevel
It's possible to use API call as well:
curl -u "admin:admin" -X PUT "https://harbor.${MY_DOMAIN}/api/configurations" -H "Content-Type: application/json" -d \
"{
\"auth_mode\": \"ldap_auth\",
\"ldap_base_dn\": \"cn=users,dc=mylabs,dc=dev\",
\"ldap_filter\": \"(objectClass=organizationalPerson)\",
\"ldap_group_admin_dn\": \"cn=adgroup03,cn=users,dc=mylabs,dc=dev\",
\"ldap_group_attribute_name\": \"sAMAccountName\",
\"ldap_group_base_dn\": \"cn=users,dc=mylabs,dc=dev\",
\"ldap_group_search_filter\": \"(objectClass=group)\",
\"ldap_group_search_scope\": 1,
\"ldap_scope\": 1,
\"ldap_search_dn\": \"cn=ansible,cn=Users,dc=mylabs,dc=dev\",
\"ldap_search_password\": \"ansible_secret_password\",
\"ldap_uid\": \"sAMAccountName\",
\"ldap_url\": \"ldap://winad01.${MY_DOMAIN}\",
\"token_expiration\": 300
}"
Open a new tab with Harbor login page (https://harbor.mylabs.dev (opens new window)) and login as:
- User:
aduser01 - Password:
admin
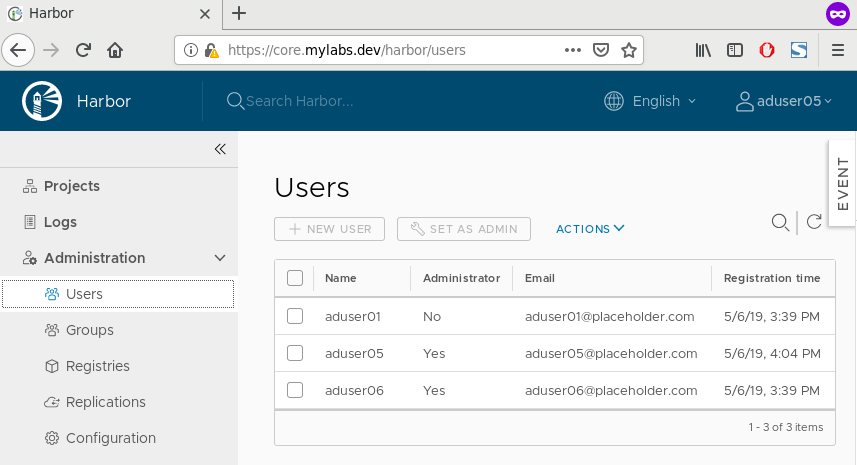
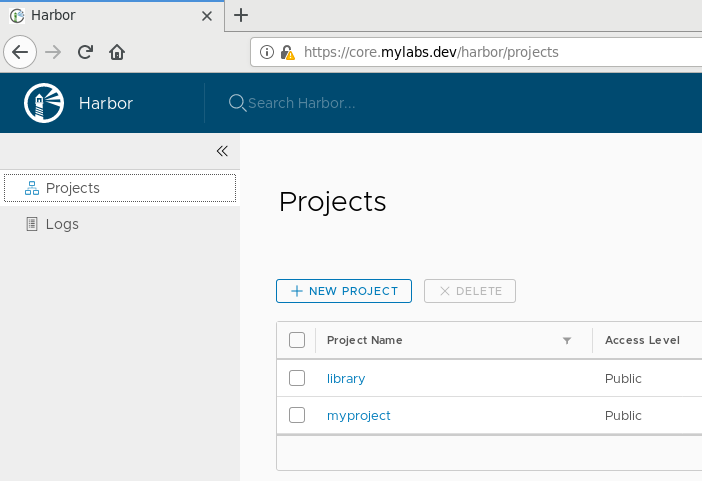
You should see limited view on the right side containing only Projects
and Logs:
Open a new tab with Harbor login page (https://harbor.mylabs.dev (opens new window)) and login as:
- User:
aduser06andaduser05 - Password:
admin
This user belongs to group adgroup03 which is group containing Harbor
Administrators. You should be able to see much more details in Harbor now
and also Users table has some details: